The EDGE Advantage:
Vulnerability Management
Does your organization deploy connected devices, for example, routers, switches, or printers? If you answered yes, then there is a high chance that you have vulnerabilities lurking in your device firmware and software that your current vulnerability management solutions are unable to monitor or detect.
Vulnerability management is an essential component of protecting your networks and organization from falling victim to the next attack. However, many solutions rely on agents and clients to provide vulnerability detection, and as a large majority of connected devices are unable to undergo these installations, they therefore go unmanaged.
Luckily for you, our flagship product, EDGE, offers a fully SaaS solution that provides you with complete vulnerability management and detection for your connected devices and their firmware and software.
Detect Known and Never before Discovered Vulnerabilities
EDGE goes beyond traditional device vulnerability and threat management solutions by providing your organization with vulnerability detection for both known and unknown vulnerabilities, which are vulnerabilities that have not yet been reported in the industry. This gives your organization the opportunity to remediate these vulnerabilities before they serve as entry points for hackers.
Unprecedented Insights
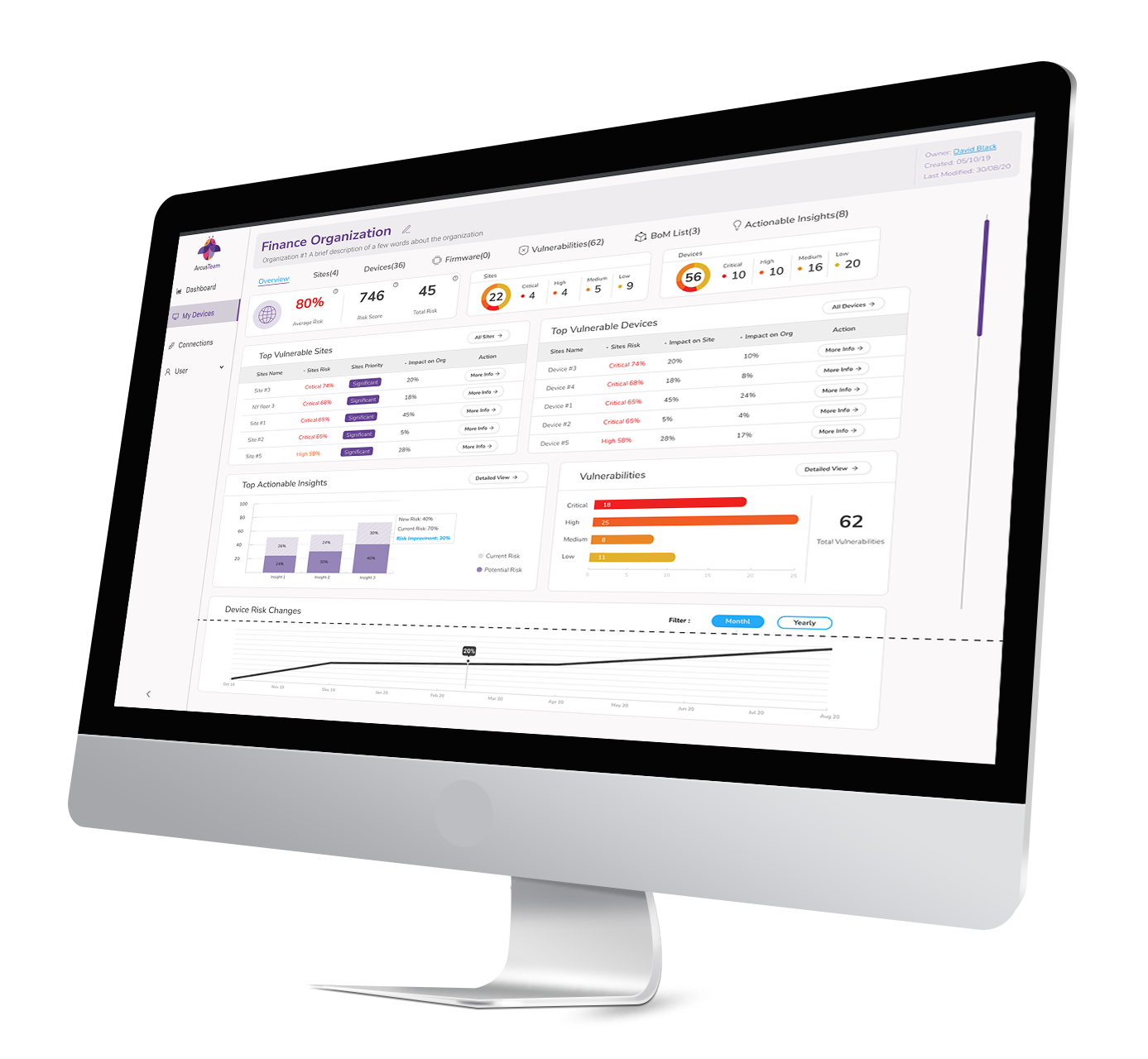
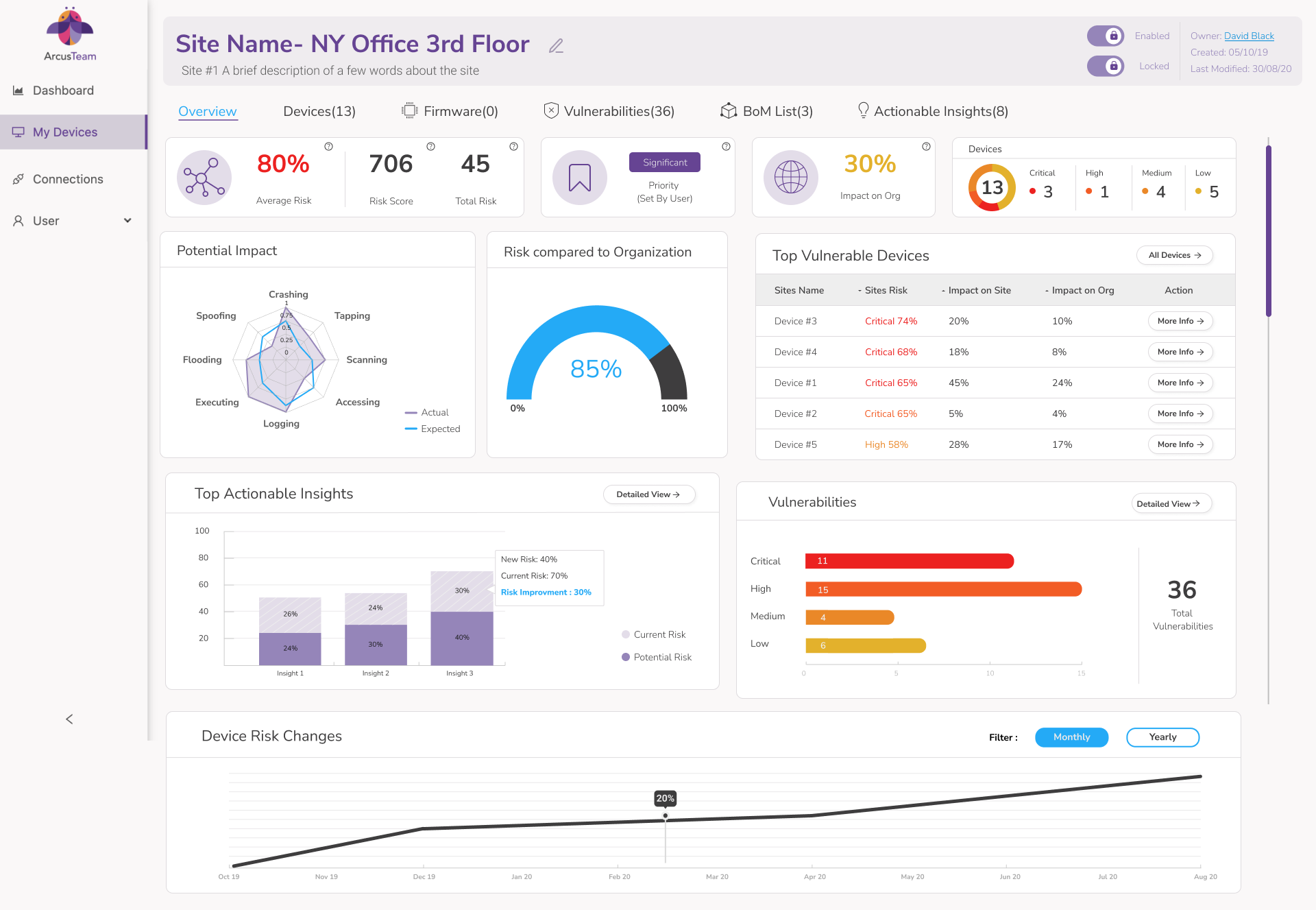
- Risk level: With EDGE, you receive accurate risk level scores per device that take into account vulnerabilities found on the device in addition to the device’s importance in relation to your business processes
- Type
- Public: A known vulnerability that has already been reported
- Private: A vulnerability reported by the customer
- ArcusTeam: A never before discovered vulnerability, reported by ArcusTeam
- CVSS (Common Vulnerability Scoring System)
- CVE (Common Vulnerabilities and Exposures)
- CWE (Common Weakness Enumeration)
- In the Wild: This is used to indicate whether the vulnerability has been officially reported as weaponized and has been used by a hacker
- Exploit Reported: The vulnerability has been reported as having the potential to be weaponized but has not yet been reported as such
Centralized Vulnerability Detection
What’s in it for You?
INFORMATION
Knowledge is Power
Gain invaluable insight into new and unknown device vulnerabilities, including brand-new threats and attack patterns.
TIME
Transform your manual vulnerability management processes into automated ones and reduce your vulnerability workload by as much as 70%!
MONEY
Why EDGE by ArcusTeam
Scalability ability to efficiently protect attack surfaces in large-scale governments and organizations
Full
automated
approach
Visibility into
known and unknown vulnerabilities
Prioritizes
vulnerabilities by location and impact
Single tool
for all connected devices
Predictive
solution
Key Features

Agentless

No Hardware or
Software Integration

Predictive

Pure SaaS Solution

Risk-Free

Effortless Deployment

