Protect your Enterprise from Threats by Automatically Monitoring your ATTACK Surface FOR CONNECTED DEVICES
Enterprises like yours are becoming increasingly reliant on connected devices. All of these connected devices and their firmware and software act as open doors for cyber attacks – leading to an ever-evolving attack surface that’s difficult to manage and control.
As a result, your CISOs and security teams are dealing with multiple challenges as they try to manage an ever-evolving attack surface and protect your organization from cyber attacks.
SCHEDULE A DEMO
Multiple tools are required to manage your attack surface and prevent security issues from different types of connected devices.
Current attack surface and vulnerability management solutions cannot identify zero-day vulnerabilities.
Lack of clarity and prioritization about which vulnerabilities and threats pose real risk to your business and critical assets.
Manual threat mitigation involving the need to review exhausting lists of vulnerabilities.
Reactive market solutions only identify attacks after an attacker infiltrates your enterprise network.
How Can DeviceTotal Help you Stay on Top of this Evolving Threat?
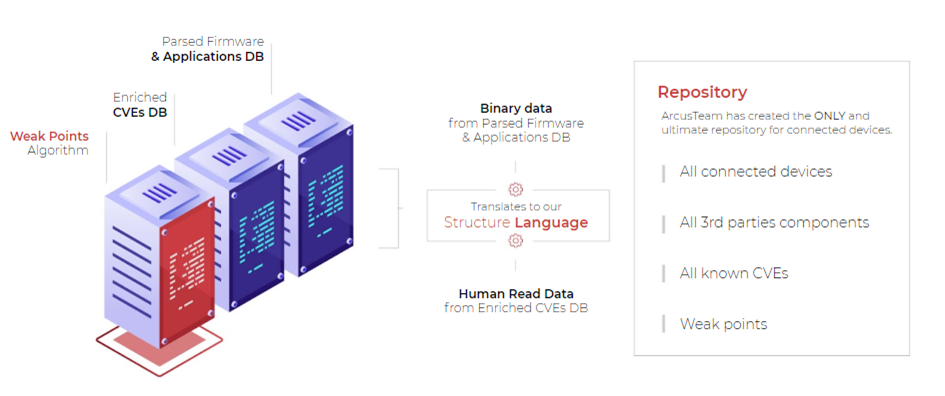
DeviceTotal by ArcusTeam is a complete attack surface management platform for connected devices that evolves faster than the everchanging cyber risks that threaten your network. Based on our proprietary and advanced technology, it enables you to get ahead of those threats, giving you full visibility into your attack surface and connected devices, together with their firmware and software, while continuously predicting, identifying, assessing, prioritizing, and mitigating any potential cyber threats – before they threaten your connected networks.
Unbiased
Approach
No need to rely solely on vendor security for attack surface management and connected device security
Proactive
Approach
Protect your network against both known and unknown vulnerabilities
Accurate Risk Analysis & Prioritization
Automated
Mitigation
Benefit from Automated Device Security in 4 Simple Steps
DISCOVER
Identify all connected devices in your network, together with their location, hardware, firmware, and software components.

ANALYZE

MITIGATE
CONTROL
Key Features

Agentless

No Hardware or
Software Integration

Predictive

Pure SaaS Solution

Risk-Free

Effortless Deployment

Free Evaluation
What’s in it for You?
INFORMATION
Knowledge is Power
Gain invaluable insight into new and potential zero-day vulnerabilities, including brand-new threats and attack patterns.
TIME
Every Second Counts
Transform your manual attack surface management processes into automated ones and reduce your vulnerability workload by as much as 70%!
MONEY
Manage your Attack Surface on 3 Different Levels
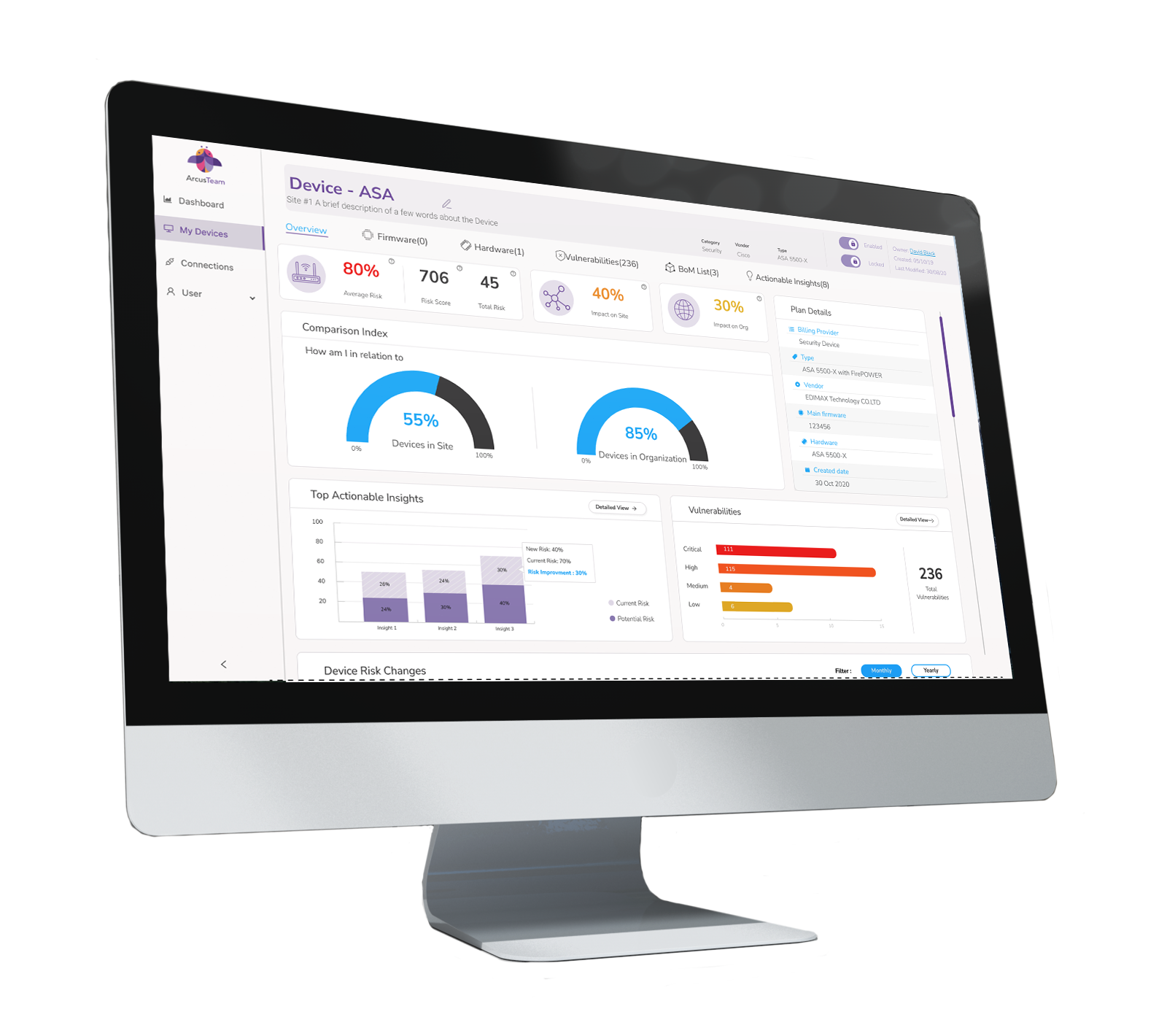
Device Level
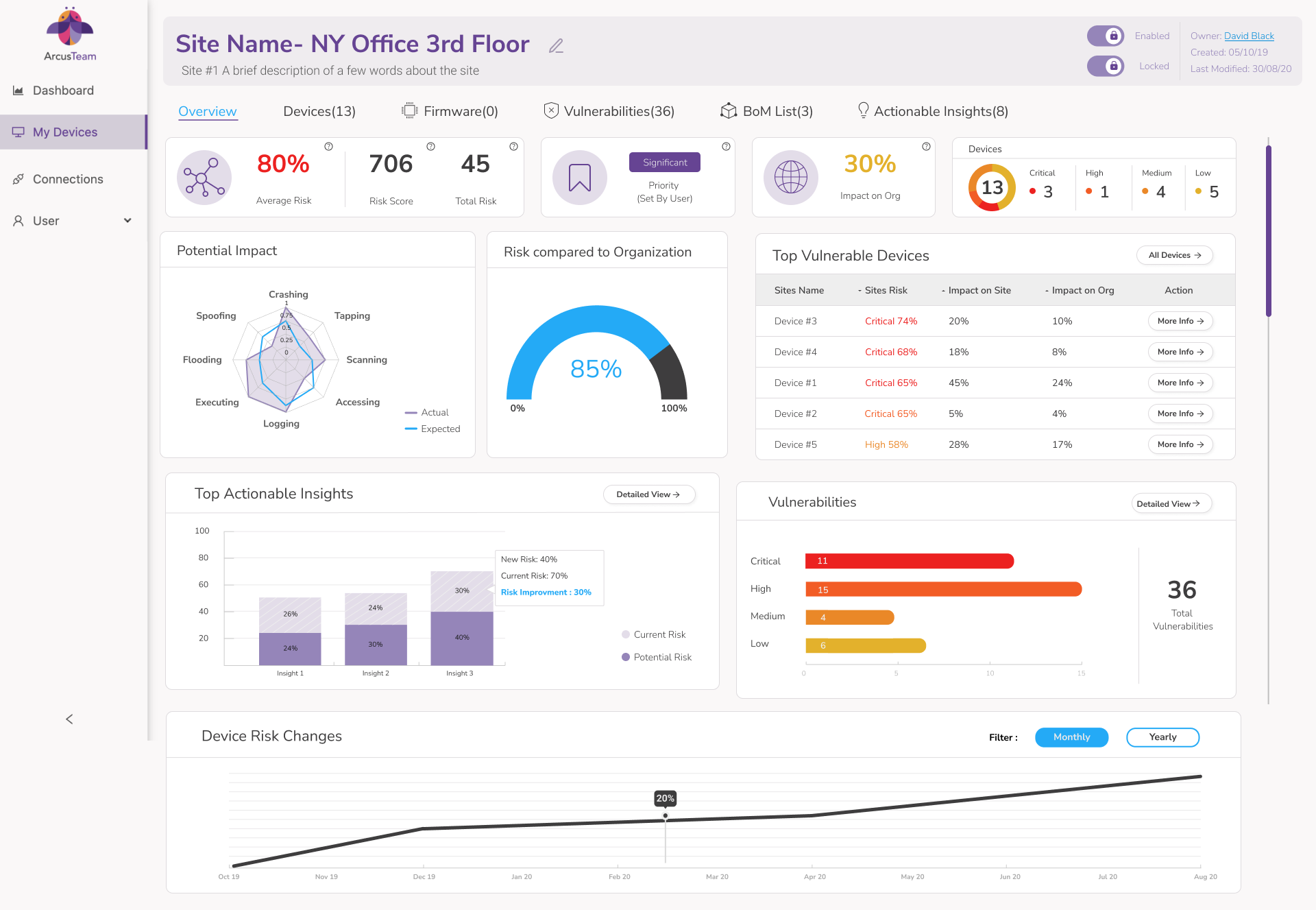
Site Level
Get full control over the security of your organization’s sites. Manage your attack surface by gaining security insights into each individual site; including the breakdown of vulnerabilities in that site, the site’s contribution to the organization’s overall risk level, and actionable insights for remediation.
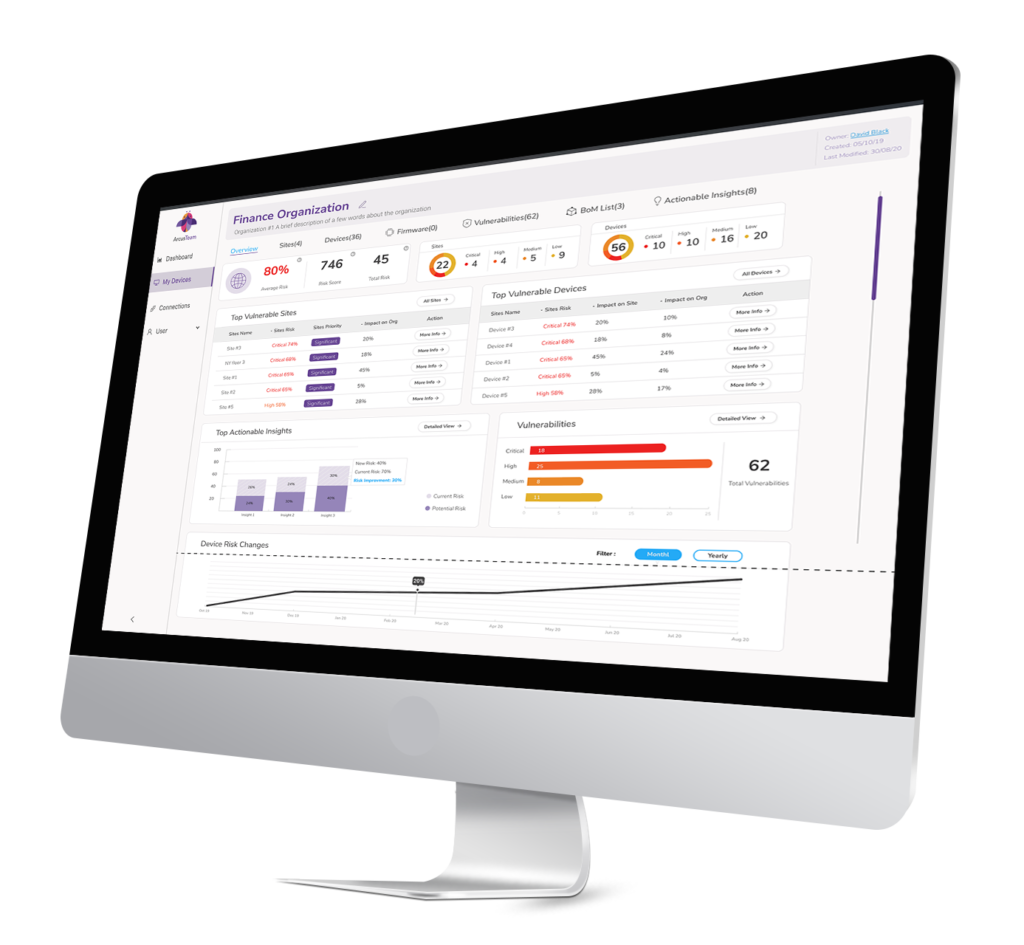
Organization Level
The Technology Behind DeviceTotal