E.D.G.E
Cyberattacks are increasing exponentially. Threat sophistication is intensifying at an alarming rate.
You need a solution that evolves faster than those threats, capable of predicting and proactively eliminating cyberattacks before they happen
You need an EDGE
E.D.G.E: An Ever-Evolving
Threat Elimination Platform
The only solution that predicts, blocks, and eliminates cyber-attacks before they threaten your current and future connected networks.

Predictive

Proactive

Agentless

Automated
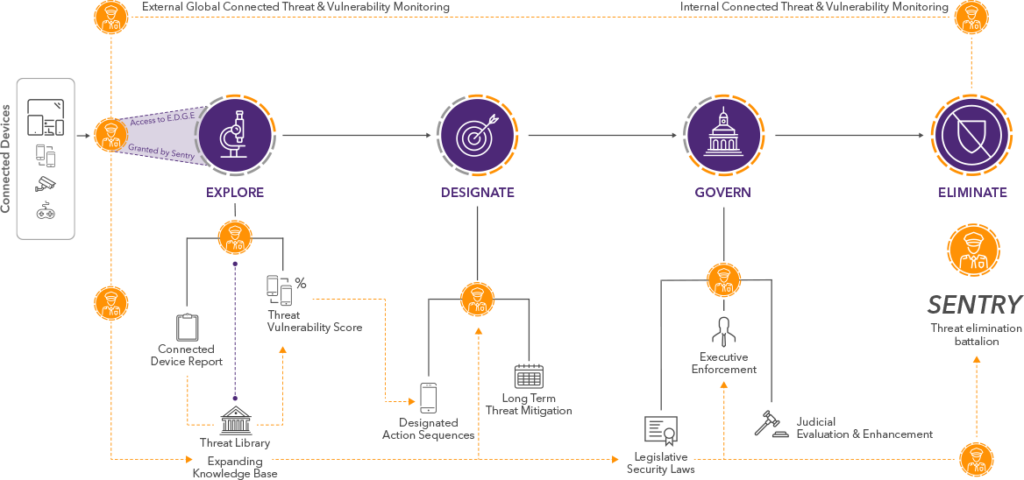
Explore
Utilize E.D.G.E. to identify all known and unknown devices connected to your network, and quantify the threat each one poses to your enterprise.
Designate
Automatically prioritize and sequence threat aversion and mitigation actions. E.D.G.E. identifies and defines threat mitigation, including recommending immediate action, eradication, firmware updates, security patches, or Perimeter platform actions. It also identifies high-risk updates that should not be performed.
Govern
Create custom rule-based security policies for your enterprise’s connected environment to protect it from all security threats. E.D.G.E.’s AI-based perpetual learning capabilities allows the system to react to changes in the corporate network and provides automated security enhancement, management, and enforcement of security policies to reflect those changes.
Eradicate
Protect virtual corporate borders from any imminent cyberthreat. E.D.G.E automatically changes the governance of your connected ecosystem and forwards all enhanced security policies to the network’s perimeter, enabling it to eradicate future network attacks.
How E.D.G.E. Works
Sentry is your EDGE
The E.D.G.E. modules work in harmony to ensure your connected ecosystem is secure. Together with Sentry, a layer of evolving intelligence that patrols your connected environment, the modules maintain constant communication with the threat library, updating changes in the network and matching it to potential threats to keep your network protected.
Sentry’s evolving intelligence algorithm processes this data. It uses prediction modeling to protect your connected world and proactively eliminate the threat of malicious activity or cyberattacks.
E.D.G.E. and Sentry at work
E.D.G.E. – Powered by Sentry
Sentry, an expansive library database of threat eradication protocols, powers E.D.G.E. Sentry uses AI and machine learning to constantly monitor the connected world, and adds newfound threats to its knowledge base. E.D.G.E. communicates constantly with Sentry, allowing for dynamic enhancements of an enterprise’s security policy and an up-to-date threat library within E.D.G.E.
The E.D.G.E. platform only allows devices to connect to your network that have been approved by Sentry, preventing potential security threats from breaching your perimeter.
3 Steps to Secure Your Connected Devices
Stay one step ahead of network cyber threats. E.D.G.E. thinks like a hacker, as it protects network vulnerabilities.
Step 1
Identify
E.D.G.E. recognizes every device on the network, and grants access to devices that have been thoroughly assessed by Sentry.
Step 2

Analyze
E.D.G.E. analyzes each network device, looking for vulnerabilities including hardcoded passwords, backdoors, and the exploitation path.
Step 3

Secure
E.D.G.E. automatically creates comprehensive security policies and enforces them on the network perimeter.
Key Features

Agentless

No Hardware or Software Integration

Predictive

Pure SaaS Solution

Risk-Free

Effortless Deployment

