Enterprise Device Security
for Software Developers
Computer software is vulnerable to a plethora of threats. Malware, like ransomware, viruses, and worms, and social engineering attacks like phishing get the most attention, but they’re not the only area of concern for developers. Inherent software vulnerabilities like hidden backdoor programs that enable remote access, or scripts that are run automatically without virus checks, can also give cyber criminals access to software, as can Internet of Things (IoT), BYOD, and work from home.
And software isn’t only vulnerable to attack as a final product–cyber threats pose a risk throughout the product lifestyle, from design to development and testing to deployment and maintenance. But lean business models and the relentless pressure to launch new products make it almost impossible for software companies to keep up with robust security demands, especially when using third-party components and platforms.
Software developers need a simple way to keep track of all the devices on their networks and understand which vulnerabilities pose the most significant risks so that they can get the next version of their product out on time without exposing themselves to threats. EDGE gives them exactly what they need to overcome these challenges.
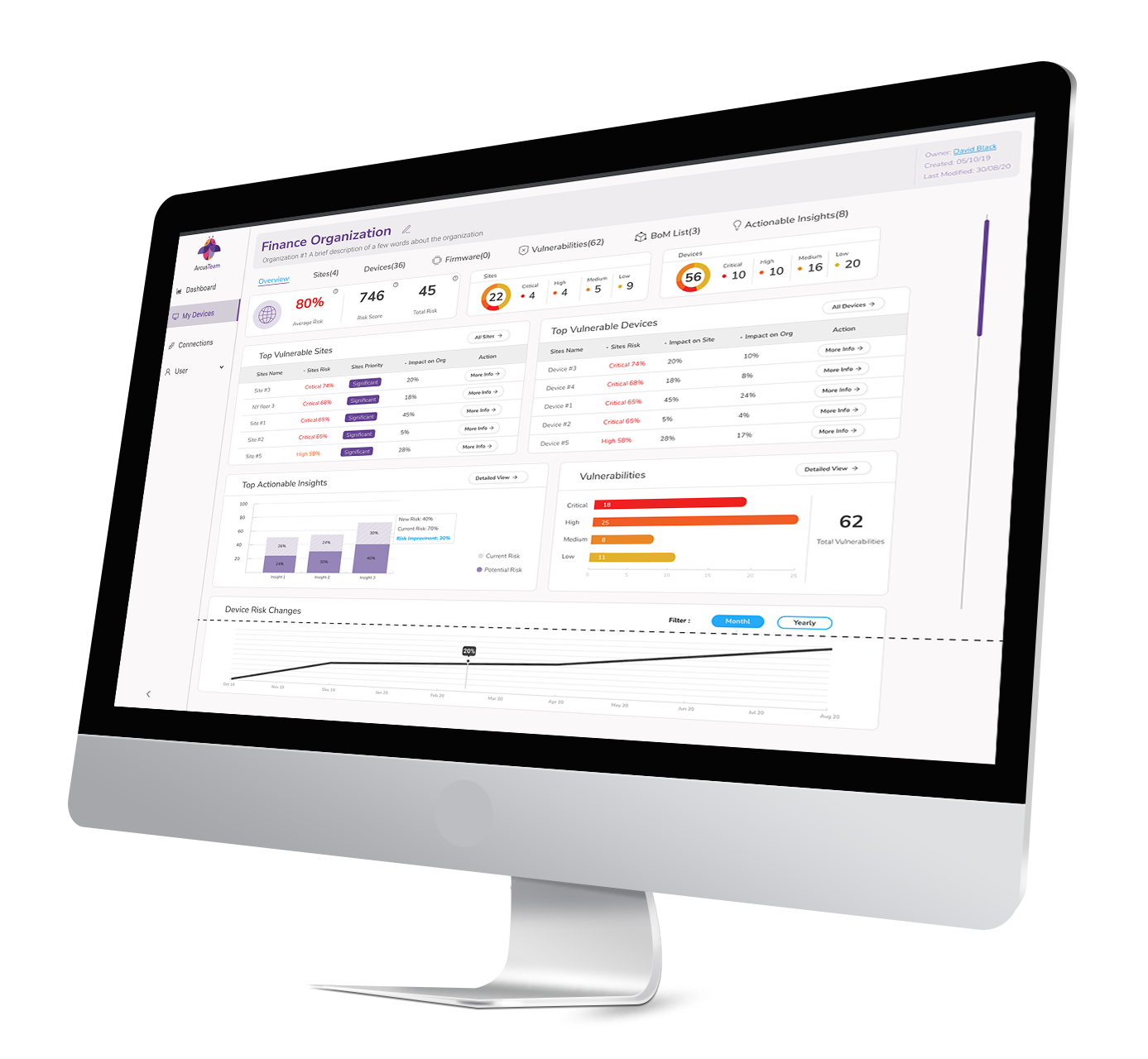
Centralized View for all Devices
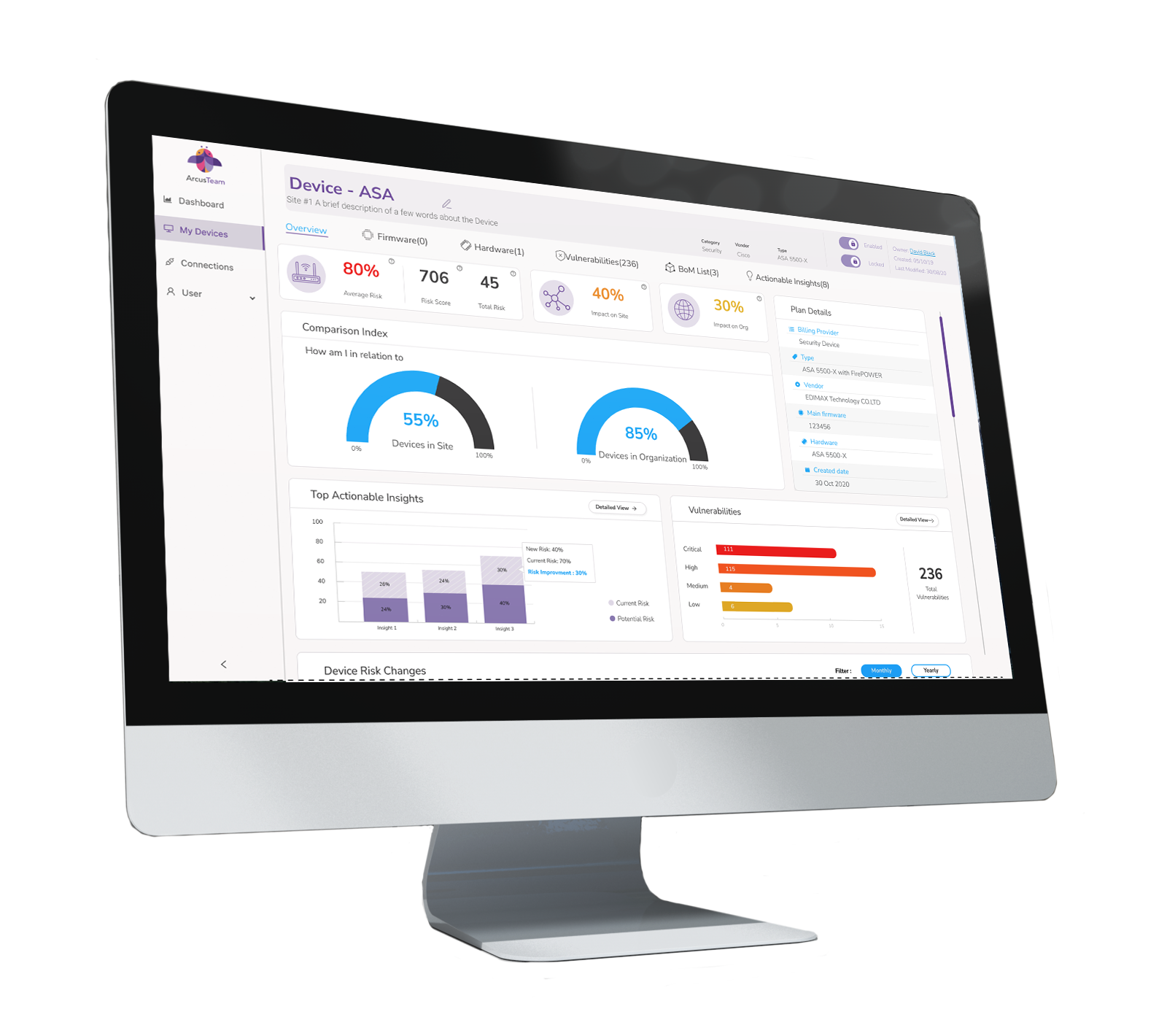
EDGE gives CISOs and cybersecurity teams in software development companies full visibility into all connected devices in their network, including their location, hardware, firmware, and BOM list of components. They can then use this visibility to manage device security from any location and across distributed management systems.
Using the platform’s centralized dashboard, the CISO has a direct line of sight (in one view) for every single device that is connected to the developer’s network at all stages of the development process, regardless of its vendor. With this neutral, unbiased approach, the CISO and cybersecurity team can proactively protect the network against threats originating from both known and unknown vulnerabilities, in all connected devices, and on third-party platforms.
Contextual Risk Prioritization
Streamlining and Cost Savings